IT security for public utilities and supply companies
The functioning of our modern society is based on the constant availability of electricity, water, telecommunications, and energy. Even a temporary and local interruption in supply has an impact on individuals, businesses, and the economic and social system in general.
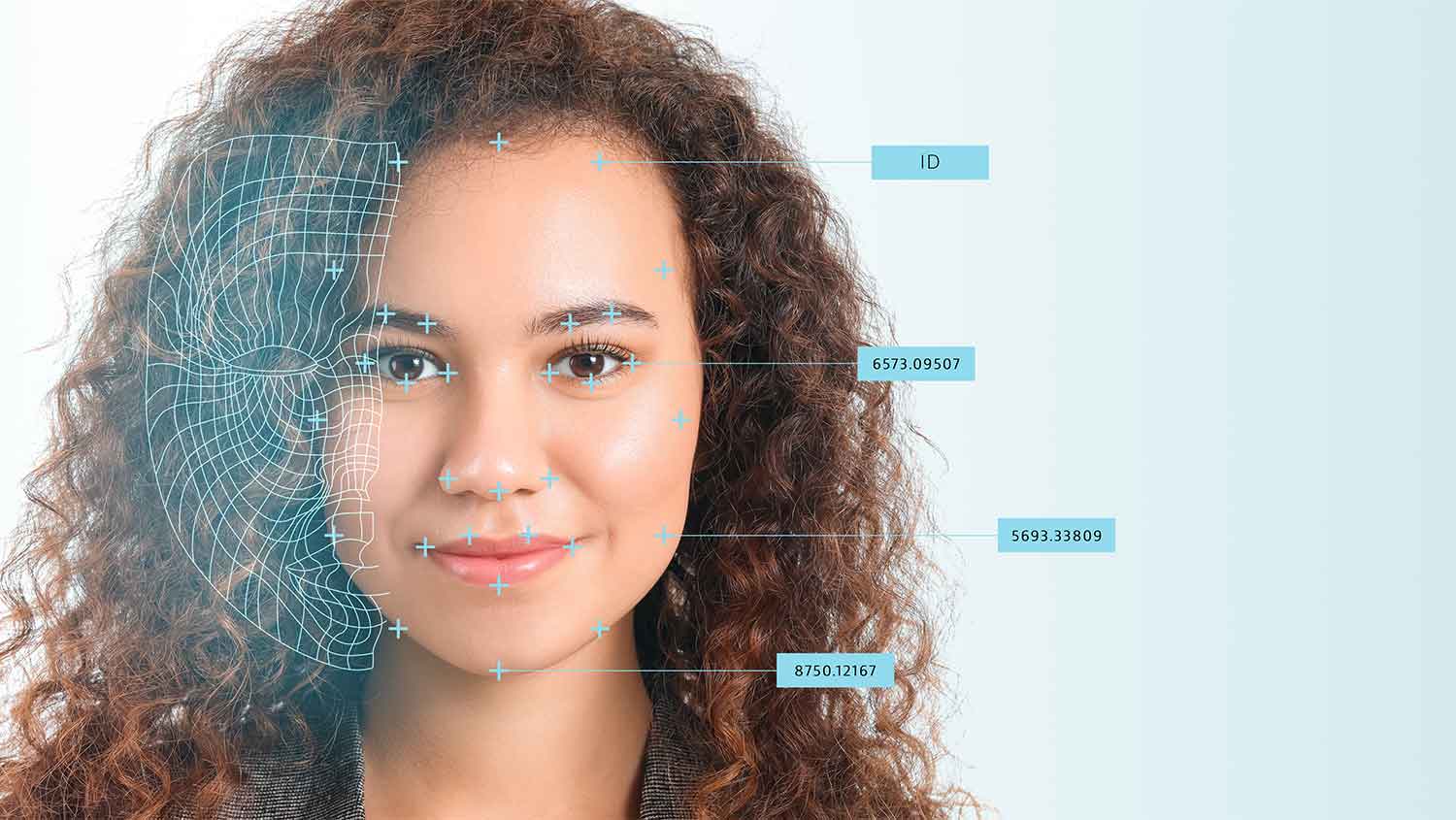
In particular, the threat from cyberattacks is increasing as our systems become more interconnected. In 2020 alone, over 141 successful attacks have taken place against companies of critical infrastructure or related fields. And the trend is upward.
Despite this, recent research shows that many municipal utilities and utility companies have not adequately protected their systems from attack.












 HWS Gruppe
HWS Gruppe
