The past year was a catalyst for the digitization of German companies. This relates in particular to how and especially where we worked. Many companies suddenly and mostly abruptly started to work from home.
According to Bitkom, almost every 2nd employee was affected by this development in the spring. However, this accelerator of many digitization projects also has downsides. Since the attack surface for cyberattacks has increased as a result of the decentralized IT infrastructure. We should therefore take a look at how well IT security has been ensured in this time. And especially ask ourselves the question: What could we learn from this for the current “home office”-wave?
IT security or smooth operations while working from home?

This should not be a matter of decision! Even if reality has shown that this was certainly the case. And unfortunately, it is again the case today. Because many companies have reacted to the crisis: Due to the decentralized way of working, new cloud and collaboration tools had to be introduced, such as MS Teams or Zoom. Often, however, the question of the security of these applications, which were operated almost exclusively via private Internet lines, has fallen by the wayside.
Virtually overnight, employees—and with them, the IT they use—have started to work from home. Since many companies were not prepared for such a situation, this also meant that their IT structures were not designed for remote work at all. Therefore, the priority here was to create structures that kept the daily business alive despite the home office—which often meant that questions about security took a back seat.
Lack of security standards while working from home

Both companies and employees had to consider so many things: How do I deal with the fact that my company laptop is running on the same network as my in-house network printer, the private laptop as well as my children’s smartphones? How can I ensure that the private network printer does not allow intrusion into the company network?
Responsibility for the security of in-house networks and the devices used are often passed on to employees. Often, however, the basics of IT security are lacking, such as training in IT security-related actions, for example, in the case of phishing emails or about fraudulent websites, or the necessary infrastructure for working from home.
A survey by Computerbild makes it clear that basic security measures were not being used: Only just under two-thirds of respondents said they had password protection for their computers and installed virus protection programs. And only just under half mentioned the (necessary!) separation of devices used for private and business purposes. VPN connections and multifactor authentication (MFA) were ultimately affirmed by only about one-third of respondents. This clearly shows that only just under a third of all home workplaces meet these IT security standards.
Whose IT security is affected while their employees are working from home?

In short, everyones.
However, small and medium-sized companies, in particular, lull themselves into a false sense of security; in fact, size is no guarantee that they will not be affected by ransomware attacks or similar attacks. According to a recent Bitkom study, it is small and medium-sized companies that are particularly lucrative for extortionists; unlike large companies, they often have no way of bridging economic downtime and the associated costs. A “small” ransom of a few 100,000 to a single-digit million figure often seems to be paid more quickly here than waiting for lengthy decryption processes with an uncertain outcome. Multinational players have completely different (financial) options here.
The human factor as the greatest target

Yet it is almost always the human factor that poses the greatest risk to your company’s security. Our algorithms and the AI that underlie today’s virus scanners and threat protection are so good and sophisticated that they can detect malware well. Unfortunately, humans often don’t: In the morning, we want to briefly skim through the mails over a cup of coffee. We are still tired, perhaps also under time pressure; especially in such situations, we are inclined to open an attachment or follow a link without closer examination. Especially in the environment of our own places, such carelessness is fatal: the infrastructure is less protected, the virus programs may not be up to date. A single infected PC can then paralyze your entire IT infrastructure.
In addition to carelessness, attackers also rely on emotions. Data and personal (identification) information are thus often willingly revealed. It is true that malware spam inherently uses social engineering methods to play on people’s fears and concerns. Central themes in recent months have been the new insecurities associated with the Corona crisis. Supposed instructions from superiors, authorities, or colleagues—today, well-crafted malware spam can hardly be distinguished from genuine requests and is also not intercepted by Mail Protection. This also becomes clear when you consider how well hackers have succeeded in tapping personal data via fake Corona help pages. Currently, the LKA in North Rhine-Westphalia, for example, is warning against such offers.
The consequences of a ransomware attack

Ransomware is malware that prevents access to local data or a network by encrypting and/or stealing data. The aim is usually to extort ransom money to unlock the data. Another extortion method is also the threat of successive publication or sale of sensitive data on the Internet if payment is not made.
Ransomware is usually spread via links or attachments in emails, with the spreaders relying on advanced social engineering methods and also exploiting professional constraints or emergencies in particular. After all, without human assistance, infecting the PC is almost impossible, or at least unrealistic. The human factor is the biggest vulnerability in your system. This is because, despite bugs and loopholes in programs, an attack via humans themselves is less time-consuming and resource-intensive.
The damage of such attacks—both financially and in terms of reputation—is enormous. Only very few companies are adequately secured against ransomware attacks, although around three-quarters of German companies are affected by data attacks. The damage is often in the millions, as ransomware encrypts systems and data, making it impossible to continue working. If backups are also encrypted, which are often just as vulnerable to attack as the original data due to their location on the servers, companies must reckon with definitive data losses. Since most ransomware attacks rely not only on encryption but also data extraction, even after successful decryption, further data protection lawsuits by those affected are to be expected.
These measures secure your IT

So you see: In addition to the technical component, the human factor, in particular, must be included when securing your IT systems. After all, the human factor is THE weak point in your IT system.
Short-term measures such as the strict separation of private and professional devices are a good start for the current situation. In the long term, however, you need a holistic strategy that starts with the choice of technical solutions used. This includes VPN clients, cloud applications, firewalls, and anti-virus programs. Ideally, these building blocks go hand in hand, so that the maintenance effort for your IT infrastructure is reduced.
It is also essential that you become even more aware of the importance of the human security risk—and take active measures. This starts with training courses on social engineering and manipulation. This training should not only focus on the basic problems but also explain the technical aspects. Only then can a basic understanding of the dangers of such attacks emerge.
Become aware of the importance of identity protection! Today, this can be secured with simple means such as multifactor authentication. This also kills two birds with one stone: modern multifactor authentication relies on passwordless login methods and single sign-on. This not only protects your IT but also offers your employees a simpler and more effective work experience.
DoubleClue – Your protection for the human factor
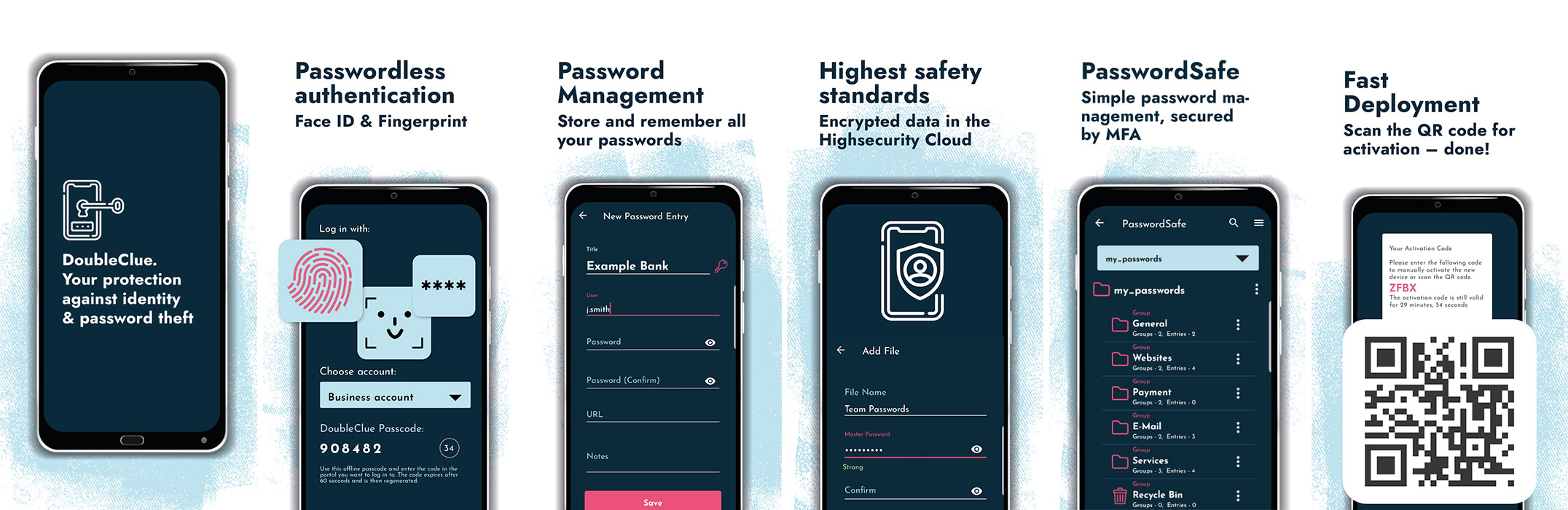
Therefore, we advise you to implement an improved identification policy in your company. Using multi-factor authentication, users must identify themselves through a second component when logging on to different applications or devices. This ensures security against unauthorized use by third parties. Multifactor authentication is especially important for all those employees who have administrative rights or remote access rights to third-party servers and devices. No matter how well you train your employees, a technical barrier that prevents unauthorized access without exception is mandatory. As a single human error by a single user is enough to cause maximum damage.
Your advantages when implementing DoubleClue
- Short roll-out time: In total, you need about one day to secure your corporate network against external attacks with multifactor authentication
- We accompany you completely during implementation and roll-out and offer you full support afterward
Request your 30-day free trial here.


















 HWS Gruppe
HWS Gruppe
